Risk Management Approaches
This is my third post in a series, detailing my exploration of risk and risk management. I’m going to focus significantly less on the paper fromDRAGOS researcher, Jason Christopher in this post. That paper did kick start my exploration of many of these topics and presented its own approach, modeled after ISO 31000. \(ISC^2\) actually teaches that developing your own approach by combining different approaches is a best practice. That makes the DRAGOS report a good example, and I will lead off with that before exploring many of the different options.
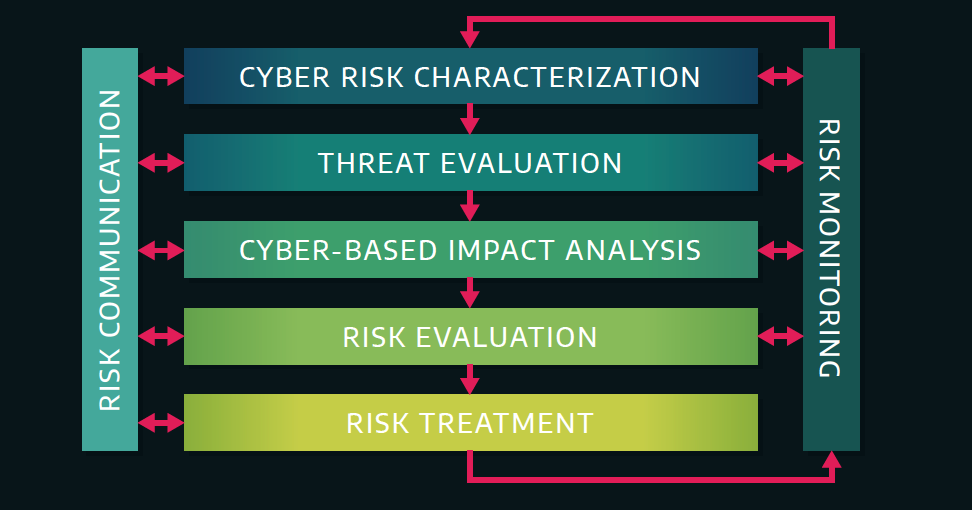
The DRAGOS report introduces their risk management process depicted in the figure above. Their process has five primary steps:
- Cyber Risk Characterization
- Threat Evaluation
- Cyber-Based Impact Analysis
- Risk Evaluation
- Risk Treatment
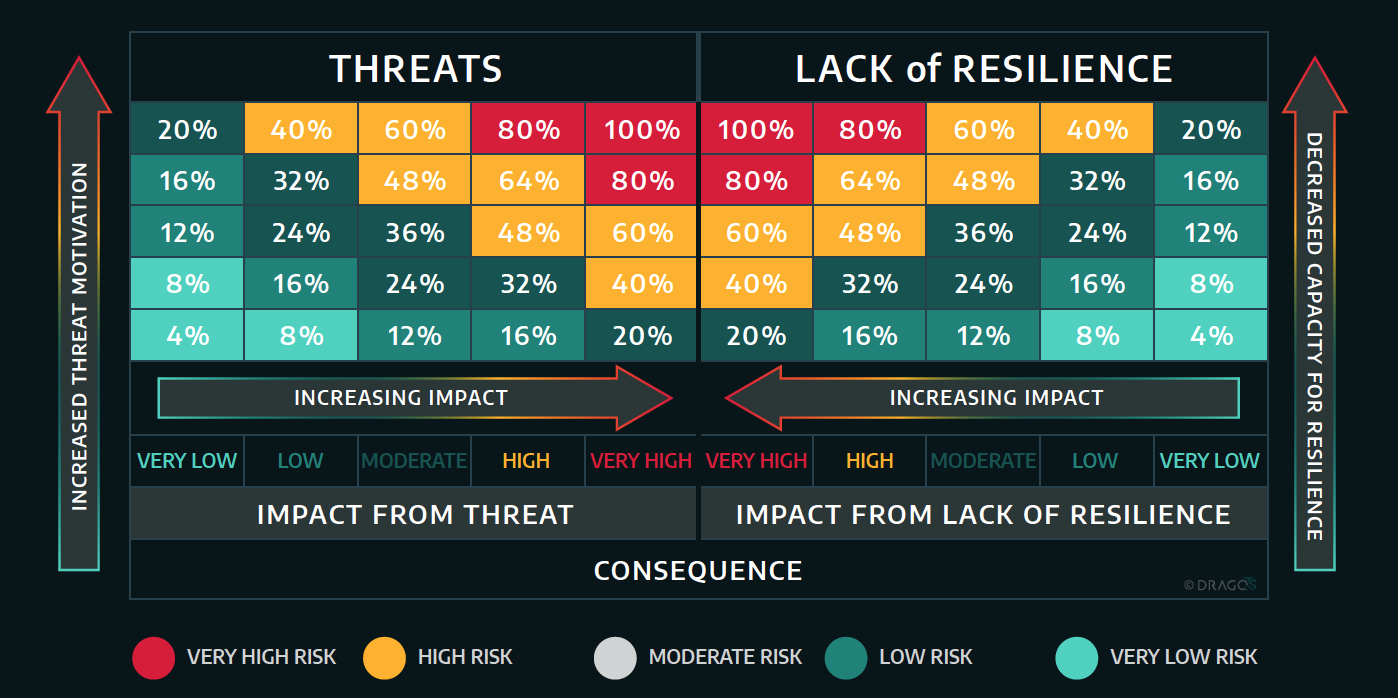
There are two other components to this process that happen continuously, risk communication and risk monitoring. The details of what occurs in each of these steps is better saved for a separate post, but there is one thing I want to highlight. Step four is where DRAGOS does qualitative and quantitative risk assessments. This is where they implement the risk equations I discussed in a previous post. The implementation of their equation allows them to use resilience in a unique method when combined with the traditional heat map. The figure below illustrates this for a qualitative analysis. I will likely explore this concept in more depth in a future blog post. The thing I find interesting is that the left axis is “threat motivation” and not probability. Perhaps the authors are using these as synonymous terms.
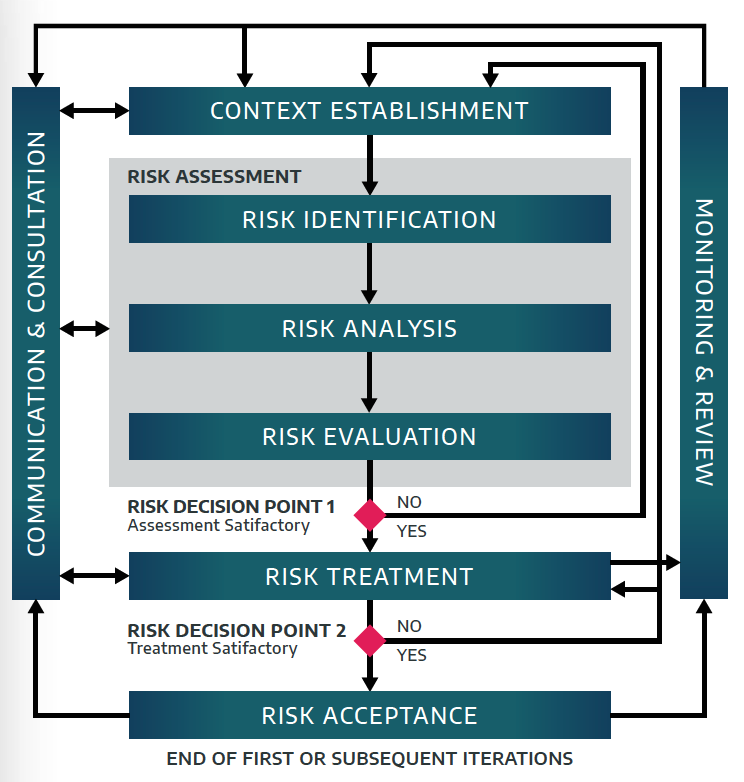
The process described to this point is derived from ISO 31000 and ISO 27005, which is depicted below. DRAGOS does a very good job of linking these and explaining variations using an annex to the report. The process from ISO 27005 is very good, but has more complexity than the DRAGOS standard. I like the ISO differences of communication and monitoring and review. I also think the explicit iterative nature of the the risk treatment is important to call out. The other somewhat subtle thing in the ISO model is that the last step is risk acceptance. This makes it very clear that their will always be some level of risk. Finally, the choice of an International Standard Organization model was wise for a company looking to have global impact. We will look at other options from NIST in subsequent paragraphs.
Eight different categories of approaches for risk analysis/management are taught by \(ISC^2\). Those eight categories are:
- Attack tree and attack based approaches
- Attack tree and attack based approaches are referred to as the oldest approaches to protecting cyber assets. \(ISC^2\) recommends that they are combined with the Common Vulnerability Scoring System (CVSS) and the Common Weakness Enumeration (CWE) data sources.
- Risk and issue-based approaches
- Risk and issue-based approaches are based on common risk or risk modeling tools like the OWASP Top 10 or the Process for Attack Simulation and Threat Analysis PASTA
- Threat-based approaches
- Threat-based approaches use threat modeling tools. A few examples are Spoofing identities, Tampering with data, Repudiation, Information disclosure, Denial of service, Elevation of privilege STRIDE, Damage potential, Reproducibility, Exploitability, Affected users, Discoverability DREAD, Visual, Agile, and Simple Threat modeling VAST, and the Quantitative Threat Modeling Method Quantitative TMM
- Human-centric approaches
- There are multiple human-centric threat modeling approaches like Trike that focuses on system users allowing/denying Creating, Reading, Updating, Deleting (CRUD) actions, Security Cards which is more of a brainstorming approach, and PnG which stands for persona non grata. PnG is recommended for agile environments because it relates to personas and can be tied into user stories and features.
- Privacy-based approaches
- LINDDUN is a privacy-based approach and stands for Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of Information Unawareness, and Noncompliance.
- Hybrid approaches
- The Hybrid Threat Modeling Method approach starts be executing the first three steps of SQUARE, which is the security quality requirements methodology, then uses Security Cards from the human-centric approaches above to create a set of threats. The third step is to use PnG from above to limit the list from step two to something manageable. The final steps are to summarize the results and then proceed with a formal risk assessment method.
- Multi-dimensional approaches
- Two examples of multi-dimensional approaches are Factor Analysis of Information Risk FAIR and Operationally Critical Threat, Asset, and Vulnerability Evaluation OCTAVE. FAIR is a quantitative model that looks at loss by analyzing assets and determining the probability a threat actor will succeed. OCTAVE is an approach that looks at risk enterprise wide. There is a specific version of OCTAVE that is used for assets called OCTAVE Allegro.
- Control-centric approaches
- The Risk Management Framework is a control-centric approach that is qualitative. The Government is required to use this approach and more detail is below.
The examples in these eight categories are all recognized as options for risk analysis. However, many of them can be used for certain aspects of analysis. This allows a user to optimize their approach by combining aspects of various techniques to fit their businesses needs in their larger risk management program. I’m currently partial to the process outlined above from ISO 27005 and leveraging some of these techniques in the gray risk assessment box of the figure. However, let’s explore the process mandated by the federal government (I am a government employee and all the views in the document are my own :) ).
According to their website “The NIST Risk Management Framework (RMF) provides a comprehensive, flexible, repeatable, and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal Information Security Modernization Act (FISMA).” I think the figure below is the most useful for understanding RMF and the documents that support it. It only shows 6 steps, leaving off the preparation step.
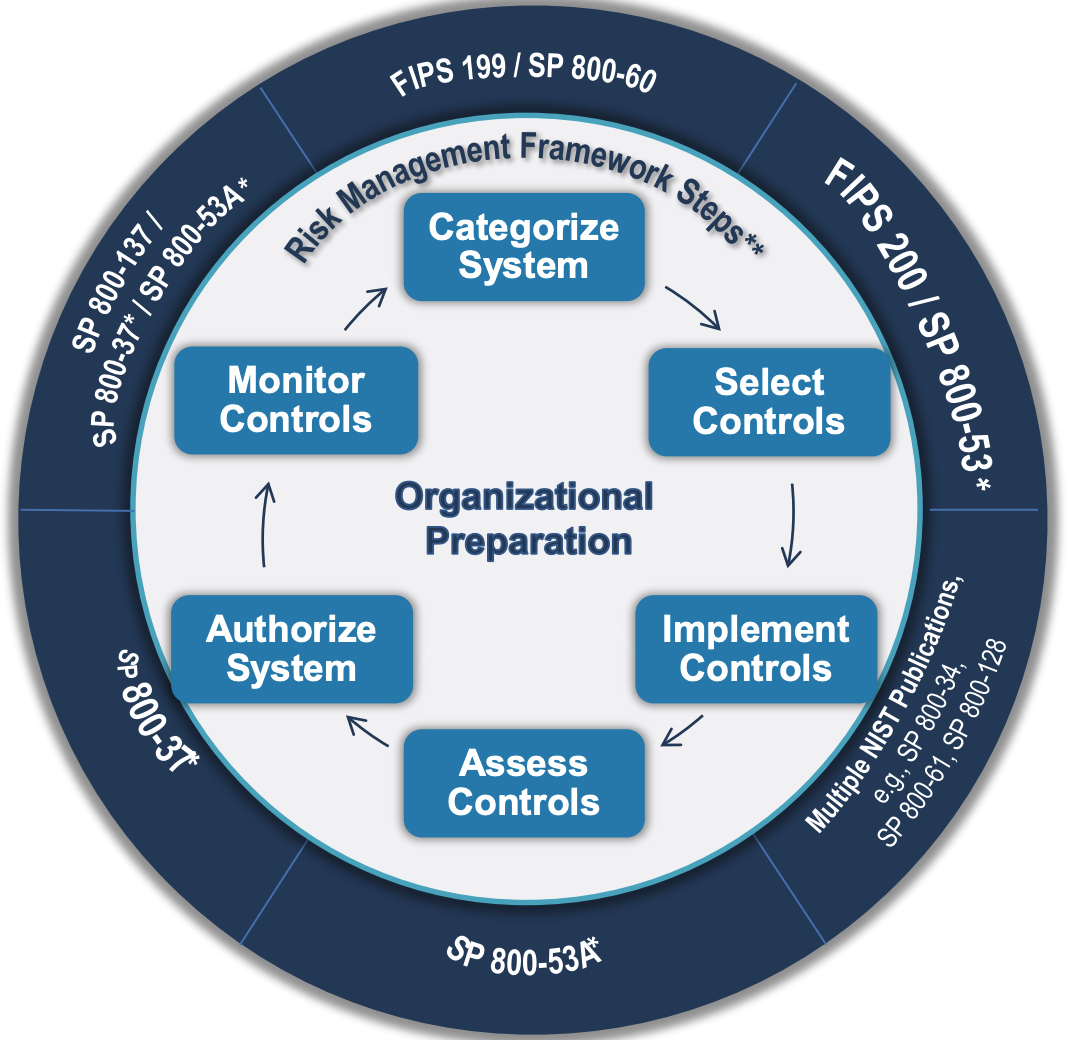
Let’s walk through the 7-step process and think about this approach at a high level.
- Prepare
- The Preparation stage is about defining responsibilities, risk management strategies, risk tolerance, and other high level things of that nature.
- Categorize
- The first real step of implementation is to Categorize. The purpose of this step is to determine the criticality of a system and its information based on a worse case scenario. The impact levels are defined as high, moderate, or low based on a loss of confidentiality, integrity, availability, or some combination of those. This is qualitative in nature. Ideally the thresholds for high, moderate, or low were determined in the preparation stage.
- Select
- In this step you select security controls using the appropriate baseline categorization from the previous step. These controls would also be tailored based on a risk assessment. The controls are drawn form NIST SP 800-53. This publication defines three security baselines and attempts to be technology agnostic. The controls are also split into different families like access control, awareness and training, etc.
- Implement
- This is the step where you implement the controls selected in the previous step. Ideally the controls would be “baked in” to the software itself. This step also includes necessary training for the controls.
- Assess
- In this step the goal is to determine if the control is effective. This includes things like proper implementation as well as just meeting the basic specification intended. NIST SP 800-53A provides high level procedures for assessing controls for effectiveness.
- Authorize
- The determination on whether a risk is acceptable after the controls are in place is made by an Authorizing Official (AO). After initial authorization a continuous monitoring process should be put in place to allow for ongoing authorization.
- Monitor
- This is where the system and its controls are continuously monitored for changes or sign of adversary activity. NIST has multiple monitoring publications like 800-39, 800-128, and 800-137. Ideally an organization will have a enterprise level monitoring program.
There are many other relevant things in this area that could be discussed. I’m going to stop here on risk assessment methodologies and focus on their pieces in future posts. If you find any errors or think anything in particular should be included, then please reach out.
